Key Highlights
- The dark web is a hidden part of the internet, accessible only with specialised software like the Tor browser, enabling anonymous communication and encrypted data exchanges.
- It represents a small portion of the deep web, which is not indexed by traditional search engines like Google or Yahoo.
- While often linked to illegal activities, it is also used for legitimate purposes like protecting freedom of speech and evading government censorship.
- Sites on the dark web typically use .onion domain suffixes, requiring unique configurations and specialised browsers.
- Although accessing the dark web is legal, engaging in criminal activity while using it can lead to serious legal consequences.
- Staying secure on the dark web involves using VPNs, updated security software, and following best practices for safe browsing.
Introduction
The internet has layers, and the dark web represents the most enigmatic of them all. Unlike the surface web, easily accessible via traditional search engines, and the deep web, which consists of vast unindexed platforms like medical records and bank account databases, the dark web remains shrouded in mystery. Accessible only through tools like the Onion Router (Tor), this corner of the internet allows encrypted communication, often safeguarding anonymity—and occasionally facilitating illegal pursuits. Is it dangerous, or does it simply offer a veil of privacy? Let’s unravel its complexities.
Understanding the Dark Web, Deep Web, and Surface Web
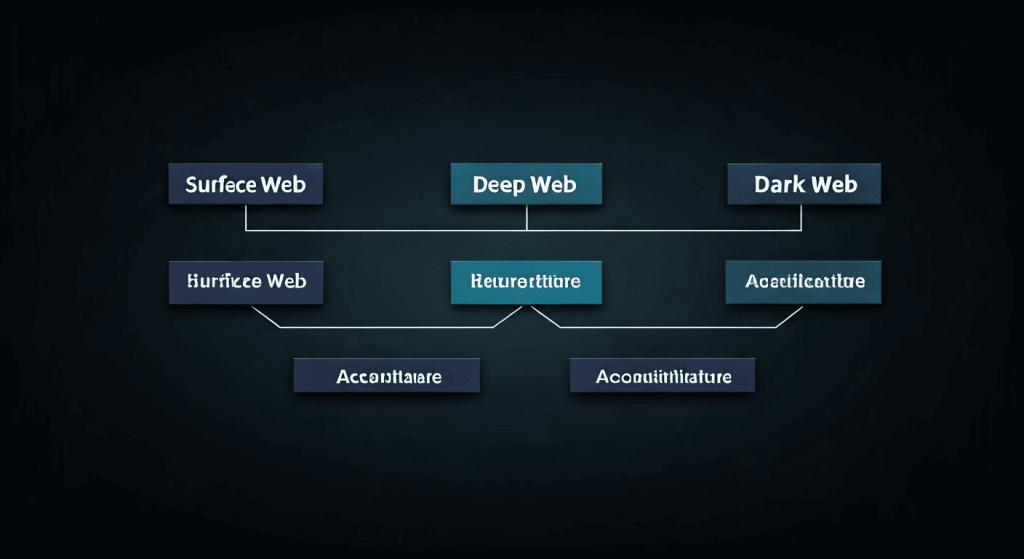
The surface web, deep web, and dark web are distinct layers of the internet. The surface web contains public-facing content, accessible via Google Chrome and other traditional browsers. The deep web, meanwhile, includes secure databases, like private bank accounts, that are hidden from search engines.
The dark web resides within the deep web, but it goes further in safeguarding anonymity. Equipped with encrypted communication made possible through onion routing and browsers like Tor, it hosts websites inaccessible by traditional means—whether used for whistleblower sites or illicit goods. These layers serve varied purposes and users.
The Surface Web: What Everyone Can Access
If you’ve spent time using popular search engines like Google or Bing, you’ve only skimmed the surface web. This visible portion of the internet houses websites ending in familiar extensions like .com and .org, with content openly indexed for ease of discovery.
Most of the internet users you know engage mainly in this layer. It’s here you’ll find social media platforms, government websites, and e-commerce portals. Search engines use techniques like “crawling” to index visible links, making this layer highly accessible.
For context, the surface web forms just 5% of the total internet content. Think of it as the tip of an iceberg; below lies the vast and unseen internet layers. Yet the surface’s simplicity belies the more complex and expansive deeper layers that so many never experience.
The Deep Web: Larger, Yet Hidden
The deep web is massive—a repository containing 90% of the internet’s content that remains hidden beneath the surface web. What makes it unique? It comprises private databases like medical records and personal bank account information, sheltered behind authentication forms, passwords, and security protocols.
Unlike the open web, it is not searchable, nor is it meant to be. For example, when you access an online banking portal, your interactions occur within the deep web, ensuring your sensitive data remains unseen by traditional search engines.
Though generally safe, caution is necessary. Its cloaked sections allow for some risky behavior, including piracy and bypassing regional restrictions. Navigating this space requires awareness, but it is primarily defined by its role in protecting privacy and streamlining processes—not by its dangers.
The Dark Web: Encrypted and Mysterious
The dark web represents secrecy, accessible only through the Tor browser and equipped with onion routing technology to encrypt pathways. Unlike the deep web’s practical protection of sensitive information, the dark web caters more to anonymity seekers.
Its sites use the .onion suffix and remain invisible to traditional browsers, requiring specific software such as Tor. This anonymity makes it possible for users to maintain encrypted communication, keeping their identity and location secure from detection.
Though infamous for hosting illicit activities such as the trade of illegal pornography and drug trafficking, the dark web also shelters whistleblowers and political dissidents from oppressive censorship. It’s a grey area in terms of legality, shaped by its range of legitimate and illicit purposes. This complexity demands understanding before venturing forth.
How the Dark Web Operates

Managing its unique infrastructure, the dark web is built atop overlay networks that require specialised configurations. Onion routing technology embeds anonymity into its framework by encrypting traffic and masking IP addresses.
Accessing these sites occurs via browsers like Tor, which utilise a network of nodes as virtual tunnels for your data, hiding its origin. This allows the dark web to safeguard messaging and site hosting, attracting users seeking privacy—from whistleblowers to those engaging in criminal activity. The next sections explore pivotal tools and operations.
The Use of Specialized Browsers like Tor
Tor browsers are quintessential for accessing the dark web safely. Derived from “The Onion Routing” project, Tor offers unique encryption pathways that route your web traffic through dispersed nodes. These virtual tunnels obscure your IP address, ensuring anonymity.
Initially developed by the U.S. Navy for encrypted communication, Tor has evolved into the preferred browser for both legitimate users and those dabbling in illicit content. Researchers, whistleblowers, and investigative journalists often use it to stay under the radar.
Downloading Tor isn’t complicated; it’s free software available online. Yet navigating the network successfully demands caution against compromised links and risky behavior. Combined with advanced tools like virtual private networks (VPNs), Tor empowers users to browse discreetly without revealing their identity.
Navigating Through .onion Links
Accessing dark websites involves understanding .onion links, which signify a domain suffix exclusive to the dark web. Traditional browsers won’t load these URLs, requiring software like Tor or specific configurations.
These links can lead to anything from whistleblower platforms to illicit marketplaces selling counterfeit money or stolen personal information. With over 76,300 estimated active sites as of 2020, finding reliable sites can be daunting. Text tables or dark web indexes like Hidden Wiki are often used as guides.
|
Site Type |
Description |
|---|---|
|
Whistleblower Sites |
Platforms for secure anonymous reporting |
|
Illicit Marketplaces |
Websites trading illegal drugs or personal data |
|
Legitimate Forums |
Discussion spaces for political freedom |
Stepping cautiously and selecting trusted directories help reduce the risks posed by these interconnected, concealed destinations.
The Role of Cryptocurrency in Transactions
Cryptocurrency plays a vital role in enabling dark web transactions, safeguarding anonymity for buyers and sellers alike. Bitcoin is the most commonly used currency, but newer alternatives have emerged.
Here are key points to note:
- Cryptocurrencies allow anonymous transactions, often favored by users engaging in illicit activities like drug trafficking or trading hacked data.
- Many dark web markets use payment tumblers to increase transaction obfuscation.
- Legitimate uses exist, including donations to political dissidents and private purchases.
While criminal activities dominate perceptions surrounding digital payments, some rely on cryptocurrency to avoid surveillance in countries curtailing freedom of speech. Nonetheless, risks exist, with scams and compromised wallets being frequent hazards. Robust security practices are non-negotiable for such users.
Legal Concerns and Misconceptions
Accessing the dark web isn’t inherently illegal; it’s the activities carried out there that draw legal scrutiny. Law enforcement monitors this virtual domain for criminal enterprises ranging from money laundering to human trafficking.
Yet, misconceptions persist. The dark web isn’t solely defined by crime; it hosts legitimate operations catering to whistleblowers and advocates of freedom of speech. However, engaging in illegal activities while on the dark web, irrespective of your intent, crosses into unlawful territory—setting up the considerations for legality discussed below.
Is It Illegal to Access the Dark Web?
Using the dark web isn’t inherently against the law. Tools like the Tor browser offer legal pathways for anonymised browsing, often utilised for private communication or evading government control.
However, not everything found on the dark web is harmless. While accessing and browsing sites isn’t prosecuted, criminal activities—like hacking personal information, drug trading, and engaging with illegal pornography—carry legal consequences. Caution is a must.
Law enforcement agencies worldwide monitor the dark web for unlawful behavior and often target users participating in crimes. So while presence alone isn’t a crime, actions undertaken in this space dictate legality. Always tread carefully.
Common Legal Activities on the Dark Web
Contrary to popular belief, the dark web has several legitimate uses. Whistleblower platforms such as political forums offer a sanctuary for individuals in oppressive regimes. Freedom of speech is another common theme, as anonymity allows users to discuss sensitive topics without fear of persecution.
Many journalists use secure encrypted platforms to source information free from surveillance. Some international news sites even host .onion links, granting users in heavily censored areas access to critical information.
Ensuring legitimate participation often requires good browsing habits, use of VPNs, and meticulous link verification. This neutral functionality highlights that not all dark web activity is criminal in nature.
When Does It Become Unlawful?
The line between legal and illegal usage on the dark web is drawn at intent. Lawful uses include accessing whistleblower sites, encrypted communication, and evading censorship.
Illegality involves criminal activities such as identity theft, illegal pornography, and trafficking illicit goods. Governments and law enforcement agencies have dedicated resources to monitor fraudulent and exploitative behavior in this realm. Operation Onymous, for instance, shut down mass amounts of suspicious dark websites linked to illegal dealings.
Remember, a legal browser like Tor doesn’t excuse criminal conduct. Your objectives dictate the legality of your presence on the dark web.
The Dangers Lurking on the Dark Web

A multitude of risks permeate the depths of the dark web, posing threats to unsuspecting users. Malware infections thrive in this dangerous environment, with malicious actors deploying various cyber attacks to exploit vulnerabilities in user systems. Additionally, personal information is often compromised, leading to identity theft and significant data breaches. Furthermore, illicit marketplaces operate seamlessly, offering illegal goods and services, from counterfeit currency to prohibited substances. Navigating this grey area requires vigilance and an understanding of the potential consequences concealed within its digital shadows.
Malware and Cybersecurity Threats
The dark web is notorious for harboring malware and cybersecurity threats that can compromise both individual and organizational safety. Malicious actors often exploit vulnerabilities, leading to severe malware infections, which can facilitate data breaches and financial losses. Cyber attacks originating from this hidden portion of the internet frequently target unsuspecting users, luring them into dangerous traps. Utilizing browsers like Tor does provide anonymity, yet without robust security software, the risks remain daunting. Staying informed and cautious is vital to safeguarding personal information and protecting against these digital dangers.
Identity Theft and Personal Data Breaches
Personal information is a prized commodity on the dark web, making identity theft a significant danger for internet users. Cybercriminals often trade stolen data, including email addresses, bank account details, and medical records, on illicit marketplaces. Breaches can occur through malware infections or phishing scams, exposing sensitive information. Once compromised, victimized individuals may face unauthorized transactions or even legal complications. The dark web’s anonymity provides a shield for malicious actors, creating a perilous environment for those unaware of the ongoing risks associated with data breaches.
Illicit Marketplaces and Content
Navigating the dark web reveals a realm filled with illicit content and marketplaces functioning outside traditional law enforcement reach. Here, users can find everything from counterfeit currencies to illegal drugs, often facilitated by the anonymity of onion routing techniques. However, these clandestine hubs are not without their dangers; malicious actors exploit them for cyber attacks and data breaches. Engaging with such platforms can lead to severe repercussions, further emphasizing the need for extreme caution and robust security measures among internet users venturing into this hidden part of the internet.
Protective Measures for Dark Web Users
Navigating the dark web necessitates vigilance and strategic planning. Utilizing a virtual private network (VPN) is essential for masking your IP address and enhancing anonymity, a critical factor in preserving personal information from malicious actors. Beyond this, adopting best practices for privacy, such as regularly updating security software and employing strong passwords, can further shield you from potential data breaches. Recognizing scams and dubious offers is equally vital, as awareness can help mitigate the risks associated with this part of the internet.
Importance of VPNs and Secure Networks
A robust VPN is essential for anyone navigating the dark web, providing an added layer of security and anonymity. By masking your IP address, a VPN shields personal information from malicious actors and reduces the likelihood of cyber attacks targeting your device. Secure networks prevent data leaks while allowing for safer access to onion routing through the Tor network. Without these protective measures, sensitive data, such as banking details or medical records, can easily fall into the hands of criminals, amplifying risks of identity theft and fraud.
Best Practices for Privacy and Security
Utilizing a virtual private network (VPN) is crucial for safeguarding anonymity while navigating the dark web. Always opt for reputable VPN services that encrypt your data and mask your IP address, creating a secure tunnel for your online activities. Regularly updating security software and being vigilant against malware infections can further enhance protection. Additionally, avoid sharing personal information on dark websites, as this can lead to identity theft or data breaches. Adopting these proactive measures ensures a more secure and private exploration of the darker corners of the internet.
Recognizing and Avoiding Scams
Navigating the dark web necessitates a keen awareness of scams that proliferate in its shadowy expanse. Malicious actors frequently employ sophisticated phishing tactics to lure unsuspecting internet users, often mimicking legitimate transactions or services. To safeguard personal information, conducting thorough research before engaging with any platform is crucial. Engaging with community forums can provide insights into trusted entities, significantly reducing the risk of falling victim to fraud. Armed with caution and utilizing robust security software, users can confidently traverse this unpredictable terrain while maintaining their anonymity.
Accessing the Dark Web Safely
Exploring the dark web can be a thrilling yet risky endeavor. Taking the right steps ensures a safe experience while delving into this hidden part of the internet. Utilizing the Tor browser is essential, as it offers anonymity through onion routing. Additionally, reliable dark web search engines can guide users to legitimate resources while minimizing exposure to illicit content. Remember, employing security software and avoiding sharing personal information mitigate the risk of malware infections and identity theft, allowing for a more secure browsing experience.
Step-by-Step Guide to Using Tor Safely
Starting your journey into the dark web requires a few essential steps for safe exploration. First, download the Tor Browser Bundle from the official Tor Project website, ensuring you bypass any third-party sites. Once installed, avoid accessing the surface web; instead, stick to .onion sites, as these are part of the onion routing system designed for anonymity. Using a reliable virtual private network (VPN) enhances your security by masking your IP address. Regularly update your security software and remain vigilant against phishing scams to protect your personal information.
Finding Reliable Dark Web Search Engines
Exploring the dark web requires using trustworthy dark web search engines, as traditional search engines won’t index these hidden sites. Specialized engines, designed for the tor network, streamline access to the vast portion of the deep web. Look for search engines that have been vetted by the community and are known for filtering out illicit content while emphasizing privacy and security. Engaging with credible resources minimizes the risks associated with malware infections and identity theft, making your experience both safer and more productive.
Tips for Safe Exploration
Emphasizing anonymity and security is crucial for navigating without incident. Utilizing the Tor browser ensures encrypted and private access to hidden websites, while a reliable virtual private network (VPN) adds an extra layer of protection. Regularly updating security software shields against malware infections and potential cyber attacks. Avoid sharing personal information or engaging in questionable activities that may attract malicious actors. Lastly, proceed with cautious curiosity—remember to stay aware of the dangers inherent to this section of the deep web, and always prioritize your privacy.
Conclusion
Navigating the dark web presents both risks and opportunities for those cautious enough to explore its depths. While it serves a critical role in promoting privacy and freedom of speech, understanding the dangers associated with this hidden part of the internet is paramount. By utilizing protective measures such as VPNs and employing best practices for security, users can safeguard their personal information. Ultimately, a well-informed approach enables individuals to discern the fine line between legitimate uses and illicit activities within this grey area of the web.
Frequently Asked Questions
What is the primary purpose of the Dark Web?
The primary purpose of the dark web is to provide a space for anonymous communication and activities that may not be permitted on the surface web. While it supports privacy for whistleblowers and activists, it also hosts illegal activities and content.
Can you accidentally access the Dark Web?
Yes, it’s possible to accidentally access the dark web if you click on unverified links or download questionable files. Certain websites may redirect users to dark web content without clear warnings, emphasizing the importance of cautious browsing habits and security measures when online.
How can I tell if my information is on the Dark Web?
To check if your information is on the dark web, use monitoring services that scan notorious marketplaces and forums. Additionally, consider signing up for alerts from identity theft protection services to be notified when your data appears in these illicit spaces.

